Analysis of asparagus-potato-london-march
asparagus-potato-london-march is a sample I downloaded from MalwareBazaar that was uploaded by @zbetcheckin, a link to the sample is below. The bulk of this analysis is based on techniques I have learned from @HuskyHacksMK’s Practical Malware Analysis & Triage course.
Sample source: MalwareBazaar
Prior to any analysis work, when dropping the file onto my FLARE VM I noticed that the file Icon is for a word doc, even though the file is an exe.
Static Analysis
File hashes:
I pulled the below hashes using hashcalc.
- MD5: 6066ef6485727c6ec277de79b0bf8f00
- SHA1: ddf79166b6f0c6a5033c809519ba71fb98053930
- SHA256: 4a4dfa10b15f6169d9523beb501854f5aafcf99e9e4ebb2684a61f84e5f2fed3
VirusTotal
I was able to find a hit when searching the file hash in VT. I received no results when searching any of the hashes in google. There is a lot going on in the VT page, I will refer back to it later once I have dug into the sample a bit more.
VirusTotal - https://www.virustotal.com/gui/file/4a4dfa10b15f6169d9523beb501854f5aafcf99e9e4ebb2684a61f84e5f2fed3
Strings
I used floss to pull all strings from the sample.
Compared to other samples not many strings are returned, only 312. There are several items of note, the ones that stuck out to me are below:
- ‘1129791717751.exe’ - this is likely the original filename of the sample
- ‘.NETFramework,Version=v4.0’ - there are multiple .Net related strings
- ‘http://asishmadinenish.com/1129791717751.png’ - speaks for itself
- ‘powershell’ - looks like it leverages powershell in some way
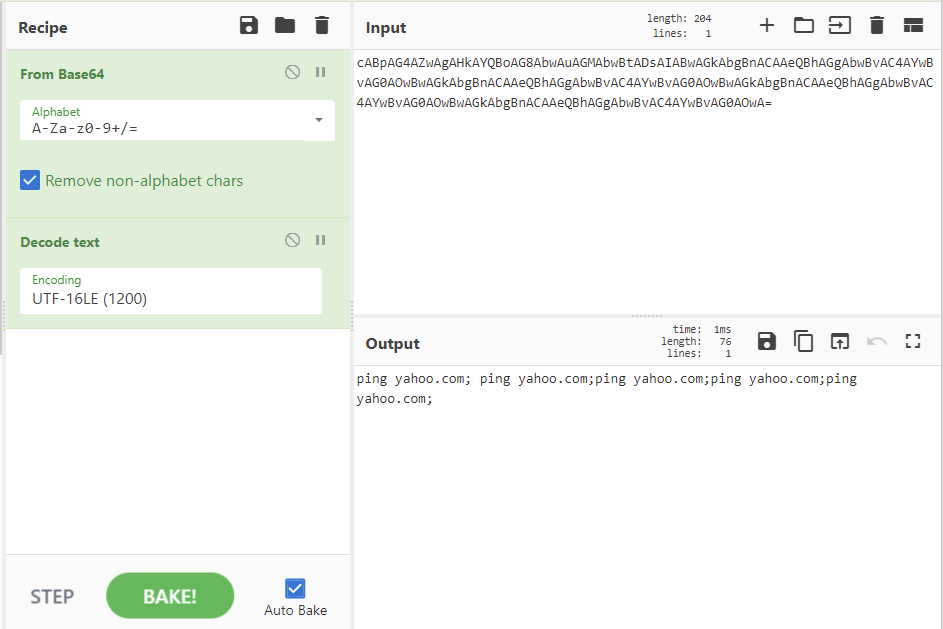
- ‘-enc cABpAG4AZwAgAHkAYQBoAG8AbwAuAGMAbwBtADsAIABwAGkAbgBnACAAeQBhAGgAbwBvAC4AYwBvAG0AOwBwAGkAbgBnACAAeQBhAGgAbwBvAC4AYwBvAG0AOwBwAGkAbgBnACAAeQBhAGgAbwBvAC4AYwBvAG0AOwBwAGkAbgBnACAAeQBhAGgAbwBvAC4AYwBvAG0AOwA=’ - and this looks very much like an encoded powershell command
- ‘OpenVPN Daemon’ - Not so sure about this one as the sample doesn’t pretend to be a VPN, I will keep this in mind going forward.
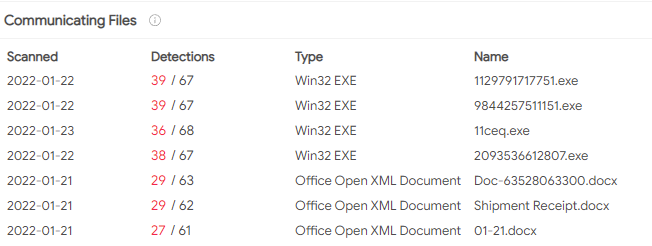
The IP for the domain ‘asishmadinenish.com’ resolves to 181.215.246.65. There are no reports against this IP in AbuseIPDB and VirusTotal shows no vendors flagging that IP as malicious. VirusTotal does have several hits for files communicating to that IP, none older than 21/01/2022.
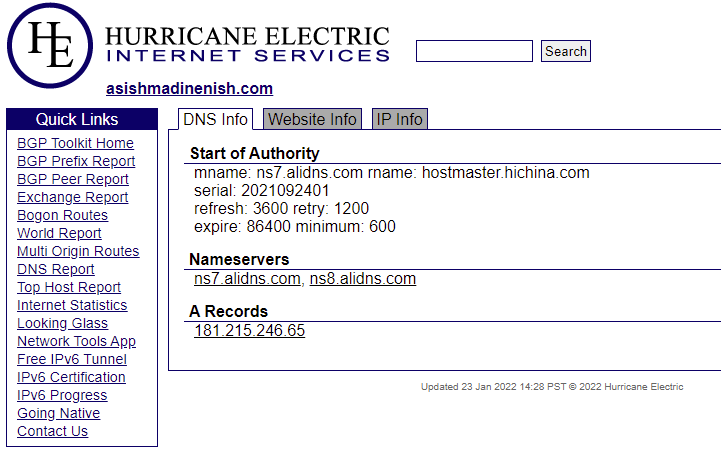
Checking out the IP using Hurricane Electrics toolkit (bgp.he.net) shows that the website is using Alibaba for its DNS and there is also a nice screenshot.
Back to that Powershell command. After decoding it, it is just a series of pings to yahoo.com. My guess at this point is that this is some rudimentary anti-sandboxing and the sample will not fully detonate if it cannot ping yahoo.
PEStudio
The compile time does not appear to have been tampered with and is shown as ‘Fri Jan 21 13:35:03 2022’, this lines up with the first submission times to VT.
Other than this there is not much shown that hasn’t cropped up earlier in my analysis.
Dynamic Analysis
Wireshark
When running the sample a call is made out to ‘http://asishmadinenish.com/1129791717751.png’, as well as the pings to yahoo.com.
To test my hypothesis regarding the pings out to Yahoo I tried running the sample without inetsim. As expected the sample exited prematurely when it could not ping Yahoo.
At this point I failed to find anything of note using tools like procmon, the only lead to go was the http request to the .png file. Based on this analysis I would classify this first stage as a loader.
Second Stage
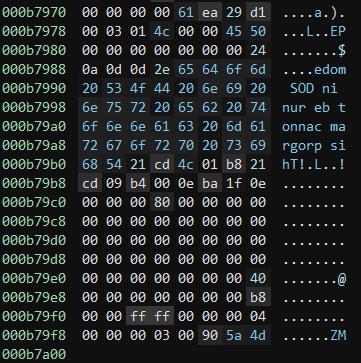
I was able to source what I think is the second stage from any.run https://app.any.run/tasks/be3eff55-9c2a-45fa-a944-c0977972b34e/#. I pulled the strings of the file but couldn’t spot anything that made sense (‘margorp’, ‘edom’) but it all made sense after looking at the hex of the file, the data is obfuscated by reversing it. Below is a screenshot of the end of the file.
I then reversed this using the below command:
perl -0777pe '$_=reverse $_' 1129791717751.png > out.file
Conclusion
Unfortunately I was unable to get any further than this as I could not get the sample to run by getting inetsim to pass it the 1129791717751.png.