Analysis of helium-ack-golf-friend
helium-ack-golf-friend is a sample I downloaded from MalwareBazaar that was uploaded by @teamffowlaw2, a link to the sample is below.
Sample source: https://bazaar.abuse.ch/sample/01e38278ae884c2ebacd3b4ca31e17aa55eb7385b6f23b623d9885ee9bce23e8/
Static Analysis
File Hashes
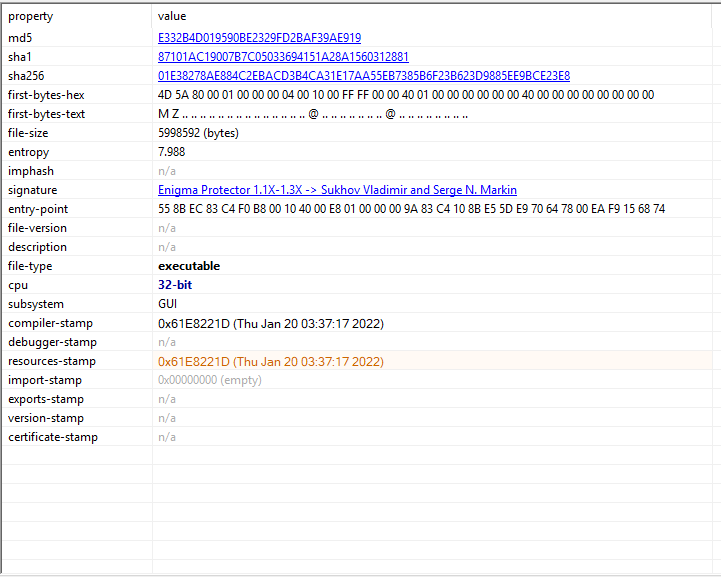
I pulled the below hashes using hashcalc.
- MD5: e332b4d019590be2329fd2baf39ae919
- SHA1: 87101ac19007b7c05033694151a28a1560312881
- SHA256: 01e38278ae884c2ebacd3b4ca31e17aa55eb7385b6f23b623d9885ee9bce23e8
VirusTotal
Of the samples I have looked at so far this is detected by AV the most with 51/66 vendors flagging it as malicious.
Hopefully this indicates that there are no anti-analysis techniques used and it is a straightforward sample to analyse. There is a lot to go through here but i’d like to go into my manual anaysis blind so lets move on.
VirusTotal - https://www.virustotal.com/gui/file/01e38278ae884c2ebacd3b4ca31e17aa55eb7385b6f23b623d9885ee9bce23e8
Strings
I used floss to pull the strings from this sample.
There is very little here aside from an xml manifest and some Windows dll files. Given the lack of intersting strings I suspect this sample is packed, so much for being easy.
PEStudio
As soon as I load the sample into PEStudio the signature ‘Enigma Protector’ jumps out.