Analysis of october-skylark-bravo-potato
october-skylark-bravo-potato is a sample I downloaded from MalwareBazaar that was uploaded by the Swiss CERT GovCERT.ch, a link to the sample is below. The bulk of this analysis is based on techniques I have learned from @HuskyHacksMK’s Practical Malware Analysis & Triage course.
Sample source: MalwareBazaar
Static Analysis
File hashes:
I pulled the below hashes using hashcalc.
- MD5: 82a4d3168c075cfce19a565d510ae3fb
- SHA1: c35bcac3c67badcaffd60f813363b6fbcef2baf7
- SHA256: 0d9facf6b7073de4e3db19eb64e80589d98cfe35b66942191390a891bb8b241c
VirusTotal
I was able to find a hit when searching the file hash in VT. Interestingly I received no results when searching any of the hashes in google.
VirusTotal - https://www.virustotal.com/gui/file/0d9facf6b7073de4e3db19eb64e80589d98cfe35b66942191390a891bb8b241c
Strings
I used floss to pull all strings from the sample.
There are plenty of strings in this file, the majority of which are of no real interest.
That said, “SOFTWARE\Borland\Delphi\RTL” indicates at least 1 part of this sample is written in Delphi. But the string that really stuck out to me is “AutoHotkeys”, could this sample leverage AutoHotKey in order to impersonate human keyboard input? There are also some other strings that could be instructions for this e.g. ‘Shift’, ‘Enter’, ‘Space’ etc.
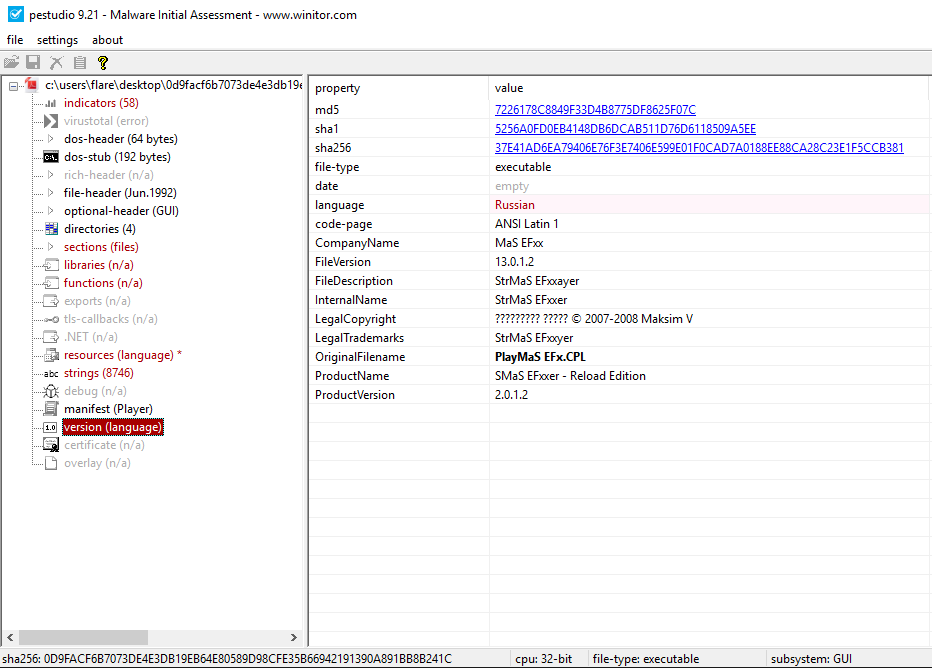
PEStudio
The compile time has been tampered with, it is showing as Sat Jun 20 10:22:17 1992
Some Russian language resources have been flagged, including dialogs and string-tables.
There is also some interesting information shown in the under version section:
Dynamic Analysis
Wireshark
Using Wireshark I could see the malware attempting to initiate an SSL connection out to goloramltd.com
-
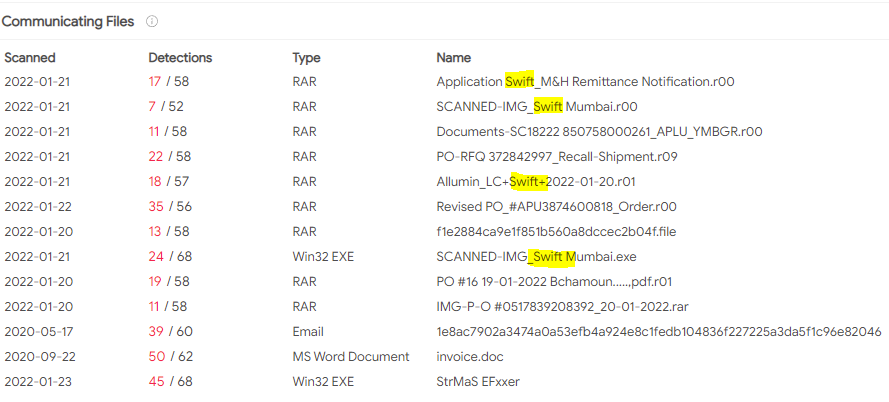
VirusTotal The URL is flagged by a few malware vendors but to me the most interesting results are on the relations page. Several communicating files are listed and a good chunk of them mention SWIFT in their name.
-
AbuseIPDB There are mp reports against the IP goloramltd.com resolves to, but the IP is geolocated to Bangladesh. This combined with the SWIFT references in the file names brought the Bangladesh Bank Cyber Heist to mind.
-
Chilean Govt CSIRT An email for this domain is listed as a sender on a Chilean CSIRT Alert posted on 23/09/2020.
Procmon
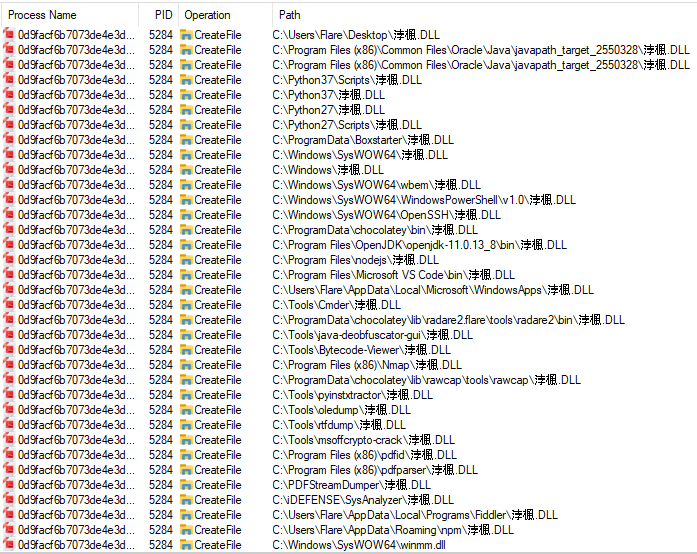
Procmon failed to reveal anything of substance, however, there were a couple of intersting files created that could hit towards the function of this sample.
There is a dll written to many different locations, however, I wasn’t able to find this on disk to try and examine it.
- ‘瑮汤l.DLL’
In addition there are 2 locations where an inetsim default file is written, if detonated with an internet connection these would be the first places to check for a 2nd stage payload.
- ‘C:\Users\Flare\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData'
- ‘C:\Users\Flare\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content’
Conclusion
Based on the behaviour of the sample I would classify it as a loader.