Preamble
This post is the capstone for @HuskyHacksMK’s Practical Malware Analysis & Triage course, course description. For the final report I chose to use the WannaCry sample from eariler in the course.
Executive Summary
WannaCry is a ransomware worm targetting Windows computers. This malware encrypts files on the victim computer and demands payment in order to decrypt the files. It propogates via the SMB protocol.
Indicators and YARA rules are included in this report.
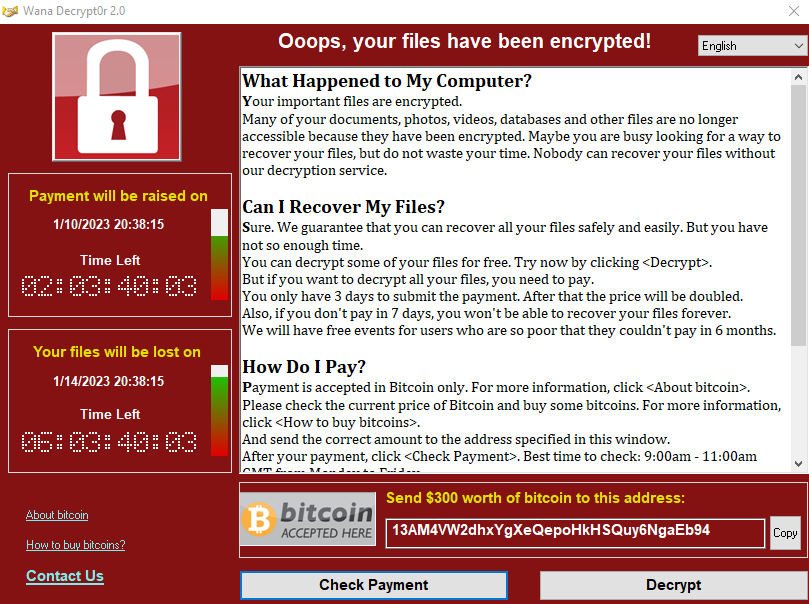
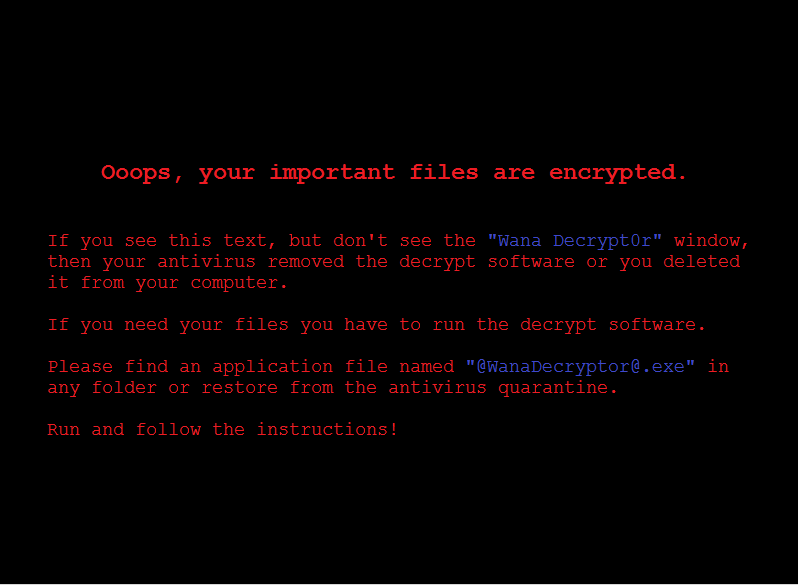
High-Level Technical Summary
On execution the sample first encrypts
Next the file ‘@WanaDecryptor@.bmp’ is saved to the users desktop and set as the desktop background.
Malware Composition
The malware sample is comprised of one exe file Ransomware.wannacry.exe.
SHA256: 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
Static Analysis
Strings
There are some interesting strings present in the wannacry sample. The most notable is a URL.
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
There is also an icacls command that would grant full access to every user to all files and folders recursively.
icacls . /grant Everyone:F /T /C /Q
Import Address Table
There are a number of imports related to handling files including ReadFile, GetFileSize, CreateFileA & MoveFileExA. WannaCry is likely manipulating files in some way. Based on imports like InternetOpenA & InternetOpenUrlA the sample appears to make an internet connection. This can be confirmed during the dynamic analysis phase. The sample appears to be using random numbers somewhere due to the presence of CryptGenRandom in the IAT.
Dynamic Analysis
Execution conditions
This sample need to be executed with Administrator rights in order to detonate. It also will not execute when the victim computer is connected to a host running inetsim.
Indicators of Compromise
Network Indicators
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
Host Indicators
C:\Windows\tasksche.exe
Rules & Signatures
Wannacry is a bit of a unique case where continued development to evade detection is not expected so I haven’t tried to create anything too complicated with the Yara rules.